▶Introduction
One of the increasingly prevalent forms of crypto-enabled fraud today is a scheme known as pig butchering. The name, a direct translation from the Chinese term “Shāz Hū Pán” (殺豬盤), captures the brutal metaphor behind the scam: like fattening a pig before slaughter, scammers “nurture” their victims emotionally and psychologically before draining them of their funds.
Though it first gained attention in Southeast Asia, pig butchering scams have since evolved into a global fraud. In 2022 alone, the FBI estimated that more than $3.3 billion was lost to crypto investment scams in the US, a significant portion of which was attributed to pig butchering. What sets these scams apart from typical phishing or hacking schemes is their psychological complexity, long playbook, and the deep emotional manipulation involved.
1. How Pig Butchering Works: From Grooming to Exit
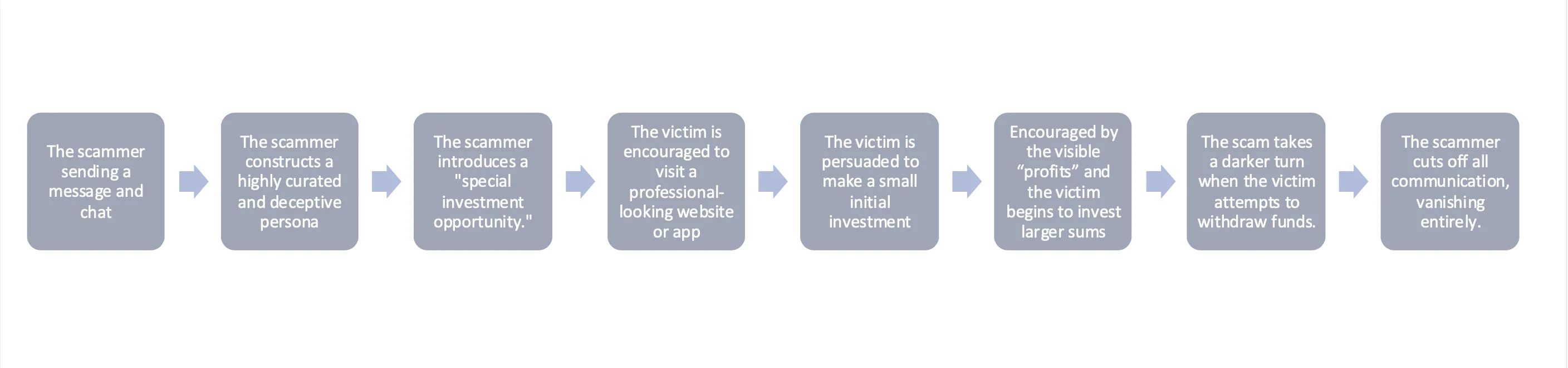
These scams begin with seemingly innocent, unsolicited outreach, often through dating apps, social media platforms, or even SMS texts sent to the wrong number. A common tactic involves the scammer sending a message such as “Hi, is this John?”, a deliberately vague question intended to prompt confusion and a response. When the recipient replies, saying something like “Wrong number,” the scammer seizes the opportunity to engage. They often respond in a friendly, apologetic tone, such as, “Oh, I’m sorry! But you seem nice—maybe we can still chat?” From there, they initiate what feels like a casual and friendly conversation, gradually increasing engagement to build rapport and trust.
As the conversation continues, the scammer constructs a highly curated and deceptive persona. They typically present themselves as affluent, ambitious, and successful professionals, often claiming to work in cryptocurrency trading, real estate, finance, or international business, and eager to share their knowledge. They send carefully selected photographs and social media content to reinforce their narrative—images of luxury cars, high-end fashion, designer handbags, fine dining, and exotic travel destinations. These are not necessarily their images but are often pulled from online sources to maintain the illusion of wealth and credibility.
Over time—sometimes weeks or even months—they carefully groom the target by developing what feels like a deep personal relationship. This could take the form of a romantic connection, complete with daily messages, emotional support, and virtual affection. In other cases, it might be a platonic or business-oriented friendship, where the scammer plays the role of a financial mentor eager to help the victim succeed.
Once trust is sufficiently established, the scammer introduces a “special investment opportunity.” They claim to have access to a private or exclusive cryptocurrency trading platform, often described as a limited-time or invitation-only opportunity available only to insiders. The scammer may say something like, “I normally don’t share this, but I really like you and want to help you make money like I did.”
The victim is encouraged to visit a professional-looking website or app, which appears at first glance to be a legitimate cryptocurrency exchange. These platforms are often beautifully designed, with fake trading dashboards, live-looking charts, and fabricated account balances that simulate actual profit growth. Every detail is crafted to assure confidence and suggest the platform is trustworthy.
At this point, the victim is persuaded to make a small initial investment, often just a few hundred dollars. After the deposit, they quickly see their balance grow on the fake platform, sometimes doubling or tripling within days. The scammer praises the victim’s “smart moves” and urges them to scale up their investment. Encouraged by the visible “profits” and the scammer’s continued reassurances, the victim begins to invest larger sums, sometimes their entire life savings, inheritance funds, or borrowed money.
As the victim becomes more heavily invested, the platform continues to show fictitious profits and positive trading activity, reinforcing the illusion of success. The scammer maintains contact throughout, offering advice, praising the victim’s decisions, and occasionally feigning concern or caution.
The scam takes a darker turn when the victim attempts to withdraw funds. Suddenly, they are faced with fabricated barriers, such as:
-
A tax clearance fee
-
A withdrawal processing fee
-
The need to verify their identity or complete “KYC” compliance
-
A minimum balance requirement to unlock withdrawals
Each new obstacle is framed as a standard procedure or temporary inconvenience. The scammer may say, “Don’t worry, I had to do the same thing—it’s just to show the government the funds are clean.” Believing that a withdrawal is just around the corner, the victim is manipulated into sending even more money, hoping to access the large profits they believe they’ve earned.
But no matter how much the victim complies, the withdrawal never happens. Eventually, the scammer cuts off all communication by blocking the victim on every platform, deleting accounts, or vanishing entirely. The fake platform becomes inaccessible or is taken offline, and the victim is left devastated, emotionally and financially.
Once the digital assets are acquired from their target, they typically move swiftly to disguise the origin and ownership of the funds. This process may include sending the funds through crypto tumblers or mixers, which are designed to break the transactional link and make tracing more difficult. In other instances, they may enlist money mules to transfer or exchange the funds at virtual asset platforms, particularly those operating in regions with minimal oversight or weak AML regulations.
2. Victim Profiles and Statistics
↦ Demographics
-
Gender and Age: While women are often perceived as primary targets, data indicates a more nuanced picture. In the UK, over half of romance scam victims are women, with men comprising 39% and 11% not reporting their gender. The highest concentration of victims falls within the 50-59 age group (20%), closely followed by the 40-49 age bracket (18%).
-
Age Distribution: Contrary to common belief, younger adults are also significantly affected. Adults aged 18-59 are 13% more likely to fall for a romance scam than those over 60. However, older adults tend to incur higher financial losses, with median losses nearly double that of their younger counterparts.
↦ Education Level
-
Academic Background: Education does not necessarily shield individuals from falling victim to romance scams. A study revealed that 32% of victims hold graduate degrees, underscoring that intelligence and education offer no guaranteed protection.
↦ Emotional Vulnerability
-
Psychological Factors: Victims often exhibit certain psychological traits, such as higher levels of neuroticism and a tendency to idealize romance, which can lead to impulsive decisions. These characteristics make them more susceptible to scammers’ manipulative tactics.
-
Life Circumstances: Scammers frequently exploit individuals during emotionally sensitive periods, such as after a divorce, the loss of a loved one, or during times of loneliness. This emotional vulnerability can cloud judgment and increase susceptibility to scams.
↦ Financial Readiness
-
Economic Status: Scammers often target individuals with access to significant financial resources, such as savings or retirement funds. Older adults, in particular, are vulnerable due to accumulated assets and potential lack of familiarity with digital communication platforms .
-
Reported Losses: In 2022, individuals over 65 reported the highest number of romance scam incidents, with 49,154 reports and losses totaling over $120 million. This age group also experienced the highest financial losses compared to younger demographics.
↦ Contact Methods and Platforms
-
Initiation Channels: A significant number of romance scams begin on social media platforms, accounting for approximately 40% of cases. Dating websites and applications follow, initiating about 19.6% of scams. Scammers often transition conversations to private messaging apps like WhatsApp or Telegram to avoid detection.
-
Payment Methods: Victims commonly transfer funds through bank wires and cryptocurrency, which together account for over 60% of reported losses. Gift cards are also frequently used, being the most reported payment method in 24% of cases.
3. Why Speaking Out Matters
Scams thrive in silence. Many victims never report what happened, often out of shame, embarrassment, or fear of being judged. But the truth is, anyone can fall for a scam. These crimes are deliberately designed to manipulate trust and emotion.
Reporting your experience is not a sign of weakness, it’s a step toward reclaiming control and helping others avoid the same trap. Your story can contribute to stronger awareness, better safeguards, and more effective investigations.
Source: VPN Alert, WhatIsMyIPAddress, Scam Detection & Protection.
4. Behind the Scenes: The Criminal Infrastructure
Pig butchering scams are not isolated crimes committed by individual actors, instead, they are coordinated by transnational criminal groups. These operations are structured like corporations, with specialized roles ranging from recruiters and romance scammers to tech handlers and money launderers. In a disturbing twist, many of the individuals executing these scams are themselves victims, lured by fake job advertisements promising high-paying opportunities abroad, only to find themselves trafficked, confined, and forced to defraud victims under threats of violence or debt bondage. Reports from NGOs and investigative journalists have exposed compounds where hundreds of trafficked workers are held and made to run scam operations as modern-day slaves.
The scale of the infrastructure behind pig butchering scams requires complex money laundering operations to clean the stolen funds and make them usable. Once money is extracted from a victim, it’s typically funneled through crypto to obscure its trail. Scammers use tools like mixers (e.g., Tornado Cash) and cross-chain transfers to try to hide the funds. Tokens are often moved between chains, eg, from Ethereum to BNB Chain or Tron and swapped into stablecoins like USDT or USDC, which are then cashed out or used in further laundering.
However, despite these efforts to hide their tracks, many of these movements are traceable on-chain. Through blockchain analysis, it’s possible to map the flow of funds—even across chains—and identify the ultimate receivers or points of consolidation.
(At the crypto layer, scammers often rely on crypto mixers like Tornado Cash, which pool transactions together and obfuscate the origin and destination of funds. )
On the fiat side, traditional money laundering methods remain crucial. Criminal networks use mule accounts and shell companies to receive and disperse wire transfers. These shell entities often pose as legitimate businesses to open bank accounts, while money mules facilitate the movement of stolen funds.
This multi-layered infrastructure is designed to break audit trails, reduce the risk of freezing assets, and buy time as the funds are slowly withdrawn, reinvested, or moved into physical assets like luxury goods or real estate.
Understanding this helps investigators stay ahead. It shows that while these operations may be sophisticated, they are not invisible. With the right tools and expertise, it’s possible to uncover the paths these funds take and take action.
Source:
https://www.aljazeera.com/features/longform/2022/8/11/meet-cambodia-cyber-slaves
https://www.unodc.org/roseap/uploads/documents/Publications/2025/Inflection_Point_2025.pdf
5. Red Flags Victims and Institutions Should Watch For
For Individuals (Potential Victims):
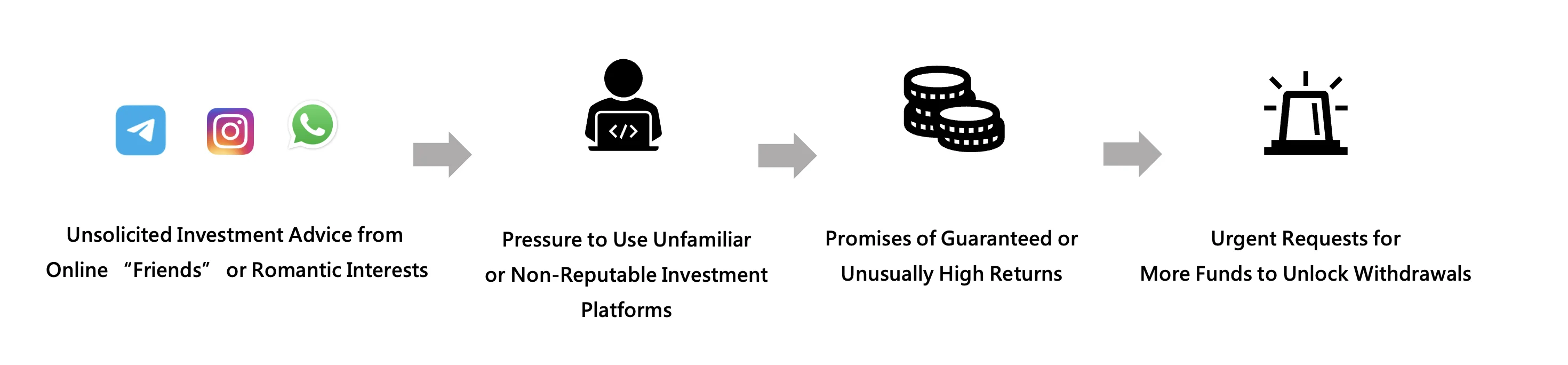
(1). Unsolicited Investment Advice from Online “Friends” or Romantic Interests
-
Scammers often initiate contact through dating apps, social media platforms, or messaging services (WhatsApp, Telegram, Instagram, etc.).
-
They gradually build trust and an emotional connection before introducing crypto investments.
-
Watch out for sudden pivots in conversation to topics like “wealth management,” “financial freedom,” or “a secret investing opportunity.”
-
Common phrases include: “I made so much with this app,” or “Let me teach you how to invest.”
(2). Pressure to Use Unfamiliar or Non-Reputable Investment Platforms
-
Fraudsters will direct victims to fake websites or apps that mimic legitimate exchanges or trading platforms.
-
These sites may feature falsified dashboards, real-time charts, and support agents, all controlled by the scammers.
-
Warning signs:
-
The platform isn’t listed on app stores or lacks independent reviews.
-
The domain is newly registered or has spelling variations of known brands.
-
Victims are asked to download APK files or grant remote control access.
-
(3). Promises of Guaranteed or Unusually High Returns
-
Claims such as “guaranteed 20% weekly profit” or “double your money in 10 days” are indicators of fraud.
-
Scammers may show fabricated screenshots of large profits or “withdrawals” as proof.
-
No legitimate investment offers guaranteed returns, especially in the volatile crypto market.
(4). Urgent Requests for More Funds to Unlock Withdrawals
-
Once the victim attempts to withdraw profits, they’re told to deposit more money to “pay taxes,” “increase their withdrawal limit,” “verify their account,” or “Avoid account freeze due to anti-money laundering rules”. These are delay tactics used to extract more money while giving the illusion of legitimacy.
6. Conclusion
What makes pig butchering scams particularly insidious is not just the loss of money, but the psychological betrayal that victims experience after being groomed, deceived, and discarded by someone they believed they could trust. These scams thrive on emotional vulnerability, false intimacy, and the mirage of opportunity, weaponizing technology, social engineering, and layered laundering infrastructure to operate on a global scale.
As these scams grow more sophisticated, it becomes increasingly crucial to stay informed, skeptical, and proactive. Whether you’re an individual investor, platform operator, or financial institution, the best defense is early detection, behavioral awareness, and rapid intelligence.
Chainvestigate offers expert blockchain tracing and investigation tools designed to help analysts, compliance teams, and law enforcement unravel complex frauds like pig butchering. With real-time monitoring, cross-chain analytics, and advanced visualization features, Chainvestigate empowers you to trace stolen assets, detect laundering behavior, and expose the infrastructure behind these scams.



